There is an obligation on organisations for personal data to be kept confidential and private. Organisations, for commercial reasons, also wish to keep personal information confidential. However, for convenience individuals wish to have access to information previously entered to use with other applications and with the same application with other organisations. Making an application Welcomer Enabled satisfies these conflicting objectives with little impact on existing applications. An application is Welcomer Enabled by an application making a copy of the personal data that an organisation is willing to allow an individual to reuse, The copy remains under the control of the organisation. It is made accessible to the individual for use with other applications approved by the organisation. Welcomer Enabled applications have these controls. The results is keeping organisational held personal information in silos but making it accessible to the individual concerned for use in other applications.
An organisation may not want to make its applications Welcomer Enabled but still wish to share data. To do this they create a special application to extract the data it is willing to share. A person may not wish to make a copy of the data, such as biometric data, but rather point to the original copy of the data. The shared data can be thought of as a personal cloud and a personal cloud can be thought of as an electronic identity.
A person can have multiple electronic persona by choosing which data items to share with which other applications. The set of shared applications along with the shared data becomes a person's electronic persona.
Moving Data between Applications
Rather than thinking of the process as moving data we think of it as duplicating data across applications. When an application is introduced to an organisation the organisation looks at all the other applications that are Welcomer Enabled and specifies the applications that are allowed to duplicate the data. These allow a person to duplicate data across applications. Links are not made until the individual specifies which data they wish to duplicate at the time they use an application. When a data item is duplicated a two way reference is made so that when the value is changed in one application the data may or may not be changed in the other application.
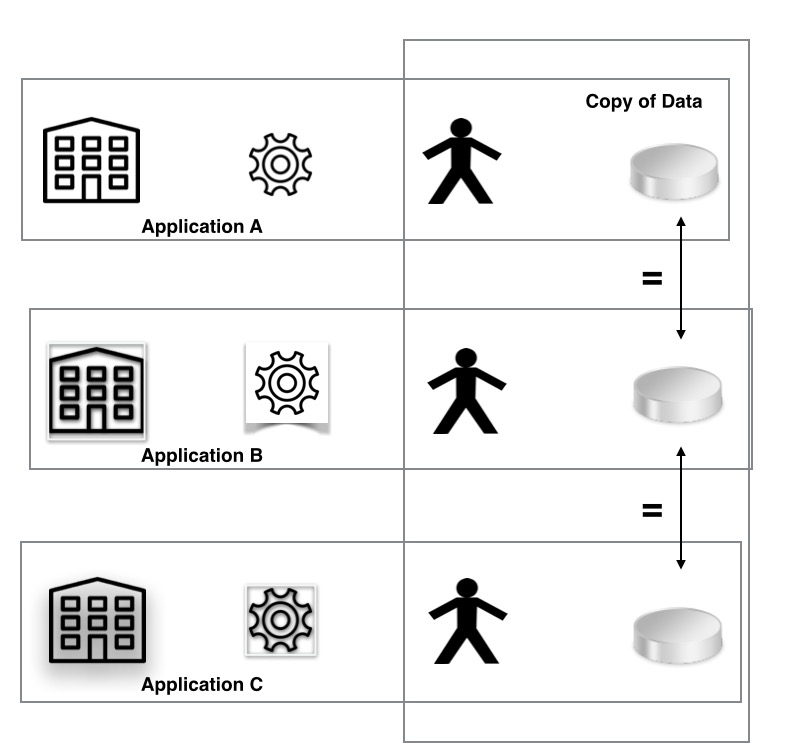
For each person the possibilities for data element X that is present in application A and in application B
- There is no value for X in either A or B.
- There is the same value for X in both A and B and the two are synchronised.
- There is a value for X in A and there may be a different value for X in B.
- There is a value for X in A and B contains a pointer to the value of X in A rather than duplicating the data in B.
1 occurs when neither application A or B has been used by a person.
2 is typically used for data that will never change such as date of birth.
3 is the most common where data can change and synchronisation across applications is not required or is not allowed.
4 is commonly used for items such as biometrics where the data elements are large.
For different application pairs X can have different rules. Thus between A and B X may follow rule 2 while between B and C X may follow rule 3.
Clusters of Data around Applications.
Clustering of Data in the Welcomer system is around applications. An application will be Welcomer Enabled and all its information will be internally linked no matter what organisation uses the application. So, for example, WelcomeAboard will enable a person to reuse data collected for one organisation with another organisation with WelcomeAboard. Verifier will enable a person to reuse information collected for one organisation with another organisation using links established within Verifier. When Verifier wishes to use data from the WelcomeAboard application then Verifier will create another copy for its internal use and the link will be made to WelcomeAboard for the person.
WelcomeAboard as an Example Application
Organisations have relationships with people as employees, customers, candidates, contractors, suppliers, and members. These relationships require structured data to define contracts and data shared between the organisation and the person. For example an employee will have an employment contract and will supply the employer with taxation and superannuation information. The organisation has a copy of these contracts and the structured data that defines the relationship.
WelcomeAboard provides a service that gives the person access to a copy of the contracts and data around the contracts. The copy remains under the control of the organisation but the person can use it for other purposes. This means a person can reuse their information with other applications with the approval of the organisation.
The advantage of this approach is that it is simpler for the person, the person gets access to a copy of their contracts and relationship data for both reuse auditing and archival purposes. This in turn makes it simpler and more secure for the person to interact with an organisation particularly when the person uses different applications with the same organisation or the same application across different organisations.