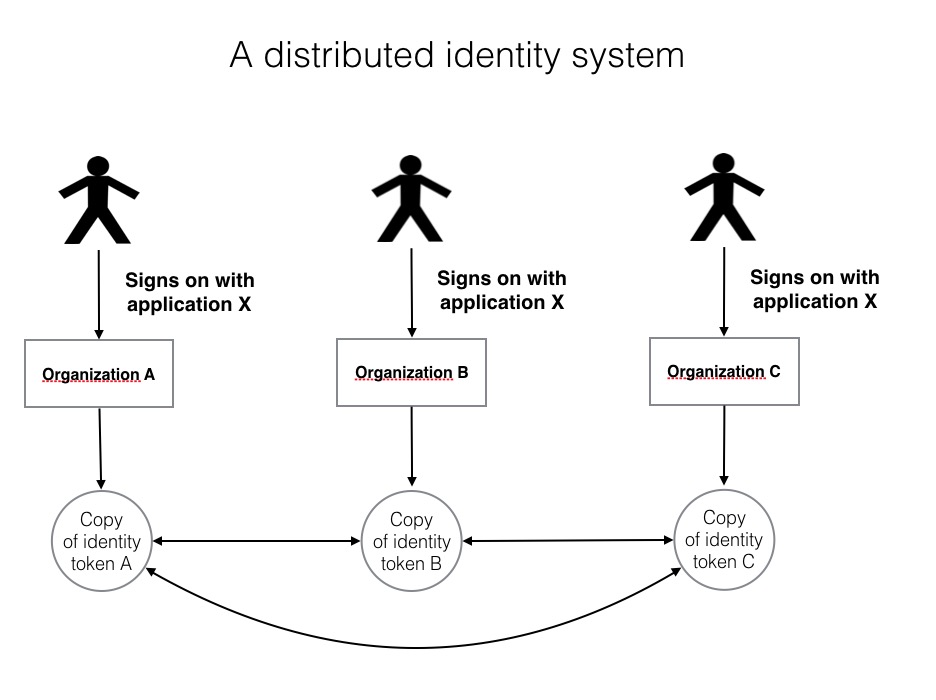
A distributed identity system connects existing electronic identities. It evolves from the connections made with applications. Initially there is no decentralised identity. The identity system emerges from the use of applications that use the connections.
An electronic identity gives an individual access to information in a data silo. A distributed identity system allows an individual to access the same data across silos. Identification with one data silo gains access to the same data across all silos.
The diagram illustrates how a distributed identity evolves with Identic. An individual has identities with three different organizations. It signs on to each organization with the same application. When signed on the application makes a copy of the identity token used by each application. The identity tokens are linked and the links saved with the organizational copy of data elements.
At some later stage the person comes back to organization C with an application Y. They logon to organization C.
Application Y accesses the data element address in organization C. Organizations A and B have agreed to allow application Y to access the address data.
When the person logs on to organization C they have access to the address data held in A, B and C. They can do this because the copy of the identity tokens are linked and stored permanently.
The same data can now be accessed across data silos. The application that accesses the data must have permission from the data silo. Permissions are granted by each data silo independently of any other data silo.
Other applications can use other data elements with other data silos. Each silo makes its own rules on access. Access rules are enforceable because the underlying linking software is open source. Only certified copies of the linking software and applications are permitted access.
An individual can also put restrictions on individual application access.
Access is granted through applications, not data. Applications define the context for access. This permits the same data to be shared or not shared depending on the application.
Data remains in silos. There is no impact on existing systems because copies of the data are linked.