Organisations hold personal data about individuals. The data is created with applications. A Welcomer Enabled Application makes personal data available to the individual so that the individual can access the data independently of the organisation. Some of the data about the individual is generated by the organisation. The release of this data to a third party is controlled by the organisation.
When an individual uses a Welcomer Enabled application the organisation with whom they are communicating has a high degree of trust that the person is the person they say they are. This enables them to welcome the individual with confidence in the identity of the individual. If they are not confident in the identity they ask the person to further authenticate their identity.
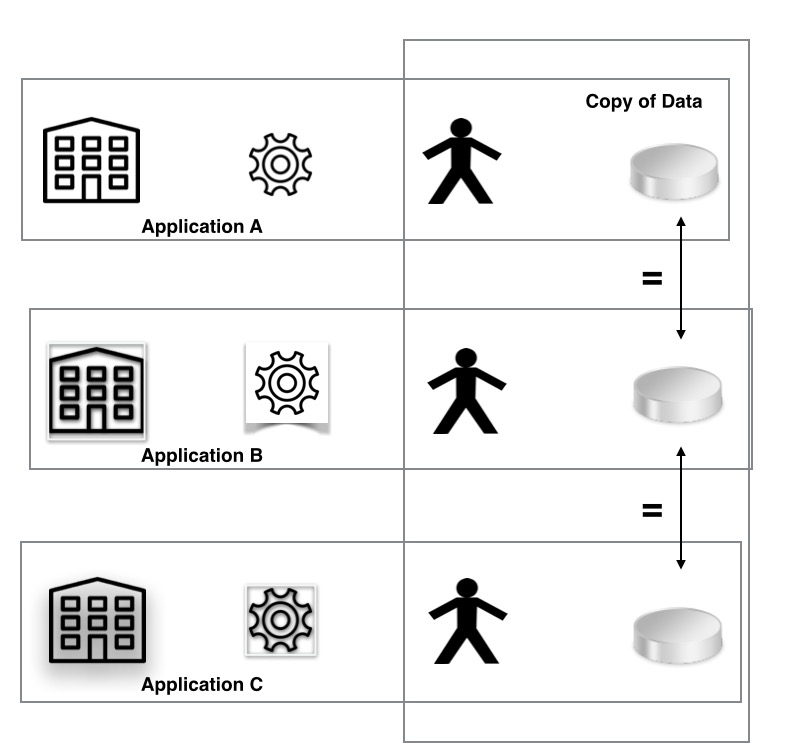
A Welcomer Enabled application makes data available to the individual by making a copy of the data and storing it separately from the original data held by the organisation. The organisation retains control over the release of the data by setting the rules on the release of the data to third parties.
Organisations control which applications they allow to access their data and so have effective control over the data exchanged with individuals.

A Welcomer Enabled application for a single organisation provides value because the individual can access the data without impacting the production systems of the organisation. Value is also created because the copy of the data being accepted as true by the organisation has residual value as it can be used for future authentication.
We can have many applications used by Organisation X and we can have applications used by many organisations.

This means an individual has access to data held by organisations independently of the different organisations but under restrictions imposed by the organisations.
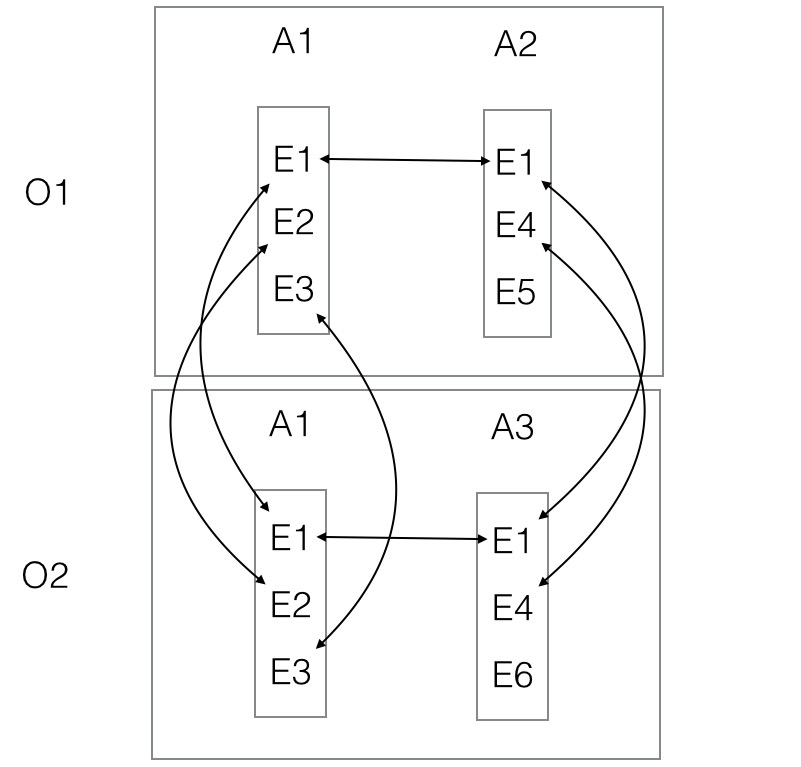
When an application is introduced into an organisation common data across other applications used by the individual is identified by the application builder. This establishes the meaning of existing data to the new application.
Almost all applications can use the copy of data held by other applications.
Remember Me and my Connections
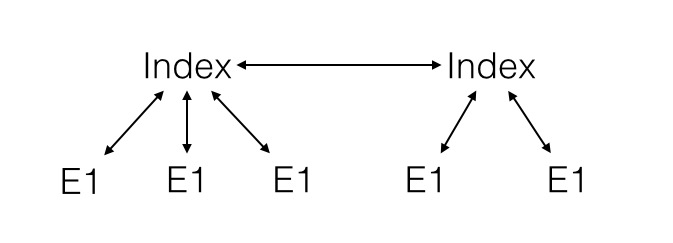
Copies of data are not created without the individual's knowledge and permission. The connections an individual makes between copies of the data are remembered but can be forgotten by the individual. An individual can ask for copies of the data to moved to a different place and to be removed completely.
An individual is able to build up disjoint networks of connections by using different applications. Each network becomes a separate electronic identity. However, because the individual can break the connections and recreate them easily this enables electronic identities to be protected from attack and for identity theft to be detected and countered.
The properties of Welcomer Enabled Applications mean that privacy can be enforced by only allowing the transfer of data from the copies. It also means that applications can be easily included or adapted to meet changing circumstances, such as the introduction of new laws, new organisations and to protect against new attacks.
Rogue applications, organisations and individuals can be contained by adapting the individual networks. In a Welcomer Enabled system organisations and individuals can be interchanged. The role an entity takes on is determined by whether the data it accesses is a copy or is the original. In the same way that an individual has a set of connections defining its identity so an organisation has a similar set of connections defining its identity.
In a Welcomer Enabled system identity is defined by the entity connections to other entities. This makes electronic identity robust, difficult to copy, and relatively easy to protect.
Welcomer Enabled Applications
If an organisation holds personal data it provides an individual with access to their personal data with a Welcomer Enabled Application. Such an application requires a person to authenticate themselves as the holder of the personal data and then accesses the personal data via an API to the organisation personal data. The organisation specifies what data can be accessed and the rules of passing on the information to a third party. For example, the government may provide access to personal data as required under the privacy principles but can restrict access to a third party unless the government is paid a fee, the organisation is located in Australia, and promises not to pass the data on to any other party.
Existing applications can improve their efficiency by becoming Welcomer Enabled. For example, a doctor can issue an electronic prescription instead of a paper prescription. The electronic prescription can be printed out by the patient or it can be made available electronically to a pharmacy.
Example uses of Welcomer Enabled Applications
Verification of identity
There are applications such as the registering of a birth or the issuing of a visa where identifying information about a person is created. This information can be the name of the person, the date of the action, the type of the action and where the action took place. If these applications are Welcomer Enabled it is possible for the individual to reuse this information in a directly analogous way to a person using a paper copy of a birth certificate or a passport.
Biometric Authentication of Individuals
If an individual stores a biometric, such as a voice print or photo id or secret or location or device, in one application then this biometric can be made available to other applications. This means that the individual can reuse a biometric across many applications and link the biometric use.
Reducing data entry by individuals
Because the individual has access to previously entered data there is no need for the data to be reentered. It can be copied by the individual.
Remembering previous interactions
Many applications build upon previous uses of the application. A Welcomer Enabled application automatically gives an individual access to these previous uses of the application.
Use of personal data across organisations
Welcomer Enabled applications makes data available across organisations by linking the data via the individual with the individual's permission. This removes the need for organisation to organisation agreements regarding the sharing of data.
Uses of Welcomer Enabled Personal Clouds
Digital Mail Box for Invoices
A digital mail box for invoices is an application which takes invoices from an organisation and enters them into a person's common invoice store. The digital mailbox transfer can be initiated by polling or by a trigger when the invoice is generated. Individuals when they purchase something agree for the invoice application to put the invoice in their store or digital mailbox. Alternatively the person's own digital mailbox application can poll all organisations that issue digital invoices to the person.
Digital Records of transactions or receipts
Many applications result in the transfer of goods or the provision of services. In most cases when a payment is made a receipt is issued and provided to the receiver of the goods or service. A Welcomer Enabled application provides a way for the receiver of the goods and services to have its own electronic copy of the transaction in a form that it can be reused for future transactions independently of the supplier of the goods and services. However, the supplier of the goods and services can put restrictions on the use of the information such as not revealing the identity of the supplier or receiving a payment each time the information is provided to a third party.
Staying in Contact with Customers, Members, Clients, Associates, etc.
Any application that is Welcomer Enabled provides a secure, private electronic way for organisations to stay in close contact with the people with whom they deal. Most successful applications have this characteristic. Most applications have bespoke methods for staying in contact with individuals. Welcomer Enabled applications use a generic approach that permits applications to cooperate to provide greater value to organisations and individuals through lower costs, better privacy, and more tailored intent messages. WelcomeAboard is a typical application that also provides a way for an organisation to continue the dialogue with employees to the benefit of both employees and employers.
Verification of Identity
Verification of Identity is showing an entity is known to other organisations. Applications such as as greenID can be made Welcomer Enabled and can then use connections an individual has made with other organisations as the means of verifying identity.
Authentication of Identity
Authentication of Identity is proving that a person is who they say they are. This is achieved through Welcomer Enabled applications by the individual being able to show that they are the same person as has conducted previous transactions and has left biometric information with organisations. Welcomer Enabled applications can share authentication information across applications.
Verification of Proof of Entitlement
Many applications require an individual to prove they are entitled to or able to receive some service or benefit. They do this by proving characteristics about themselves. Verifier Proof of Income does this for loans by a person being able to show from their record of previous transactions, such as receiving a salary, that they are able to repay the loan and hence are entitled to apply for a loan. Similarly a person can prove they are unemployed, or a student, or of pensionable age, or are disabled with the use of Welcomer Enabled applications.